A Secret is a key-value pair for managing and configuring sensitive information, such as passwords, tokens, and keys. You can create a Secret in the KCE console and use it when you mount a volume, define an environment variable, or run a command.
Operations in the KCE console
Create a Secret
- Log in to the KCE console.
- In the left navigation pane, click Cluster.
- Click the ID of the cluster in which you want to create a Secret. The cluster details page appears.
- In the left navigation pane, choose Configuration Management > Secret. The Secret list page appears.
- Click Create. On the Create Secret page, complete the following configurations:
- Name: the name of the Secret to be created.
- Namespace: the namespace of the cluster to which the Secret belongs.
- Key Type: the type of the Secret. Opaque and kubernetes.io/dockerconfigjson are available.
- Opaque: indicates a Base64-encoded Secret that stores a password or key.
- kubernetes.io/dockerconfigjson: indicates a Secret that stores authentication information for a private Docker registry.
- Parameter available when Key Type is Opaque:
- Content: the variables of the Secret. You can define the variable names and variable values as required.
- Parameters available when Key Type is kubernetes.io/dockerconfigjson:
- Image Repository Address: the name or IP address of the image repository.
- User Name: the username used to log in to the image repository.
- Password: the password used to log in to the image repository.
- Click Create.
Use a Secret
Method 1: Mount a volume of the Secret type
- Log in to the KCE console.
- In the left navigation pane, click Cluster.
- Click the ID of the cluster in which you want to use a Secret. The cluster details page appears.
- In the left navigation pane, click Workload and select any type of workload. The corresponding list page appears. For example, in the left navigation pane, choose Workload > Deployment to go to the Deployment list page.
- Click Create. The Create Deployment page appears. Set basic information and proceed to Deployment Configuration. In the Deployment Configuration step, click Add Volume, select Secret for Type, and then enter the volume name, as shown in the following figure.
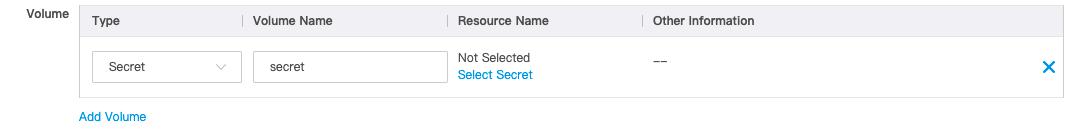
- Click Select Secret. In the Set Secret dialog box, complete the following configurations:
- Select Secret: Select a Secret as required.
- Mount Options: Select Mount All or Mount with Specified Key as required.
Note: When you select Mount with Specified Key, you can mount the Secret to a specific path by setting Items. For example, if the mount path is /etc/config and the subpath is dev, data will be stored in /etc/config/dev.
- After all configurations are completed, click Create.
Method 2: Define an environment variable for a container
- Log in to the KCE console.
- In the left navigation pane, click Cluster.
- Click the ID of the cluster in which you want to use a Secret. The cluster details page appears.
- In the left navigation pane, click Workload and select any type of workload. The corresponding list page appears. For example, in the left navigation pane, choose Workload > Deployment to go to the Deployment list page.
-
Click Create. The Create Deployment page appears. Set basic information and proceed to Deployment Configuration. In the Container configuration section, click Add for Environment Variable, as shown in the following figure.
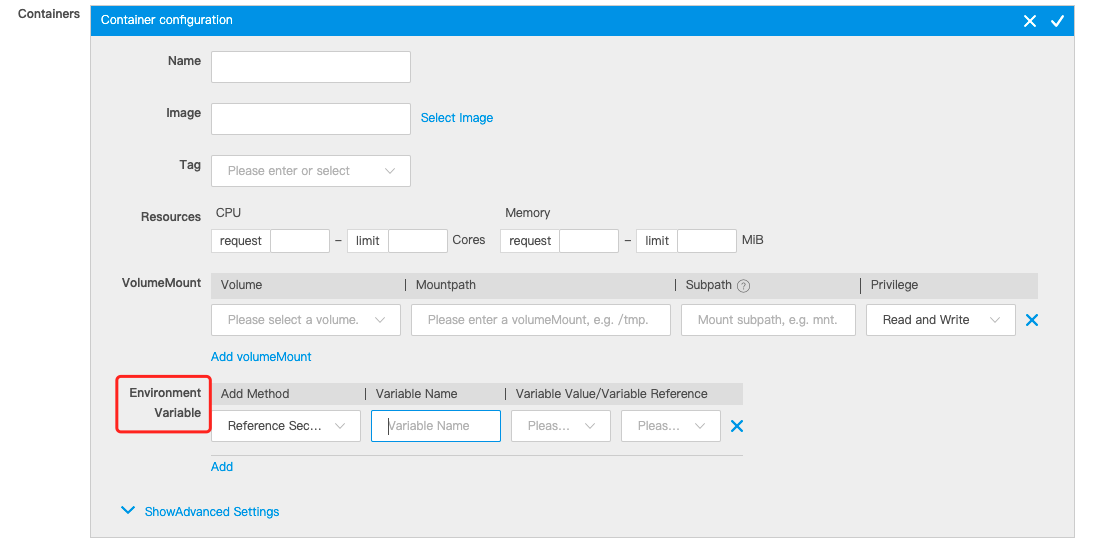
-
Select Reference Secret for Add Method, enter the variable name, and then select a variable value or a variable reference.
- After all configurations are completed, click Create.
Update a Secret
- Log in to the KCE console.
- In the left navigation pane, click Cluster.
- Click the ID of the cluster in which you want to update a Secret. The cluster details page appears.
- In the left navigation pane, choose Configuration Management > Secret. The Secret list page appears.
- Find the Secret that you want to update and click Edit YAML in the Operation column. On the UpdateSecret page, modify the configurations as required and click Update.
Delete a Secret
- Log in to the KCE console.
- In the left navigation pane, click Cluster.
- Click the ID of the cluster in which you want to delete a Secret. The cluster details page appears.
- In the left navigation pane, choose Configuration Management > Secret. The Secret list page appears.
- Find the Secret that you want to delete and click Delete in the Operation column. In the message that appears, click OK.
Operations by using kubectl
Create a Secret
Method 1: Use a YAML file
Encode the data of the Secret in the Base64 format.
# echo -n 'admin' | base64
YWRtaW4=
# echo -n '12345' | base64
MTIzNDU=
Sample secret-test.yaml file:
apiVersion: v1
kind: Secret
metadata:
name: secret-test
type: Opaque
data:
username: YWRtaW4=
password: MTIzNDU=
Create the Secret.
# kubectl apply -f secret-test.yaml
Method 2: Run the kubectl create secret command
Store the username and password in the local ./username.txt and ./password.txt files.
# echo -n 'admin' > ./username.txt
# echo -n '12345' > ./password.txt
Create the Secret.
# kubectl create secret generic secret-test --from-file=./username.txt --from-file=./password.txt
Use a Secret
Method 1: Mount a volume of the Secret type
Sample secret-volume.yaml file:
apiVersion: v1
kind: Pod
metadata:
name: pod1-test
spec:
containers:
- name: container-test
image: ksyun/nginx:latest
volumeMounts: # The mount path of the volume.
- name: secret-volume
mountPath: /etc/config
volumes: # The pod-specific volumes, which are mounted to containers in the pod.
- name: secret-volume
secret:
secretName: secret-test # The name of the Secret mounted.
restartPolicy: Never
Method 2: Define an environment variable for a container
Sample secret-env.yaml file:
apiVersion: v1
kind: Pod
metadata:
name: pod2-test
spec:
containers:
- name: container-test
image: ksyun/nainx:latest
env:
- name: SECRET_USERNAME
valueFrom:
secretKeyRef:
name: secret-test
key: username
- name: SECRET_PASSWORD
valueFrom:
secretKeyRef:
name: secret-test
key: password
restartPolicy: Never


